|
Finance departments are being asked to conduct risk assessments more frequently these days. It may be because of:
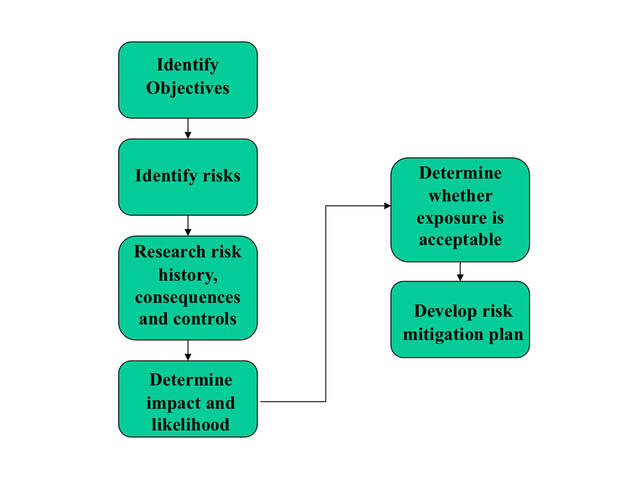
Regardless of whether the risk assessment being conducted is at the entity-wide level or for a particular business process, department, or program, the process for conducting it is the same. The steps to go through can be more or less formal depending on the importance of the risk assessment and who the ultimate users are. Some steps can even be handled on a “gut feel” basis. The steps to go through are the following: Each of these six steps is described in more detail below: (For an in-depth explanation on how to conduct proper risk assessment for implementation projects, see this blog post.) 1. Identify objectives: For every objective that a government sets, there are risks that must be managed to maximize the probability of meeting that objective. For example, a government’s objective to provide daycare services will expose it to risks (such as threats to health and safety of children, non-compliance with state laws, and inability to collect fees) that are far different from those it would be exposed to if its objective is to improve the condition of roads (safety of workers, environmental safety, engineering design safety, compliance with grant provisions). 2. Identify risks: Once you know your objectives, brainstorm the related risks. What could keep you from accomplishing the objectives? Identification of risk is best done by the “employee experts”. 3. Research risk history, controls, and consequences: Once you have identified the risks, you will need to understand each risk thoroughly. Therefore, you will need to research the following:
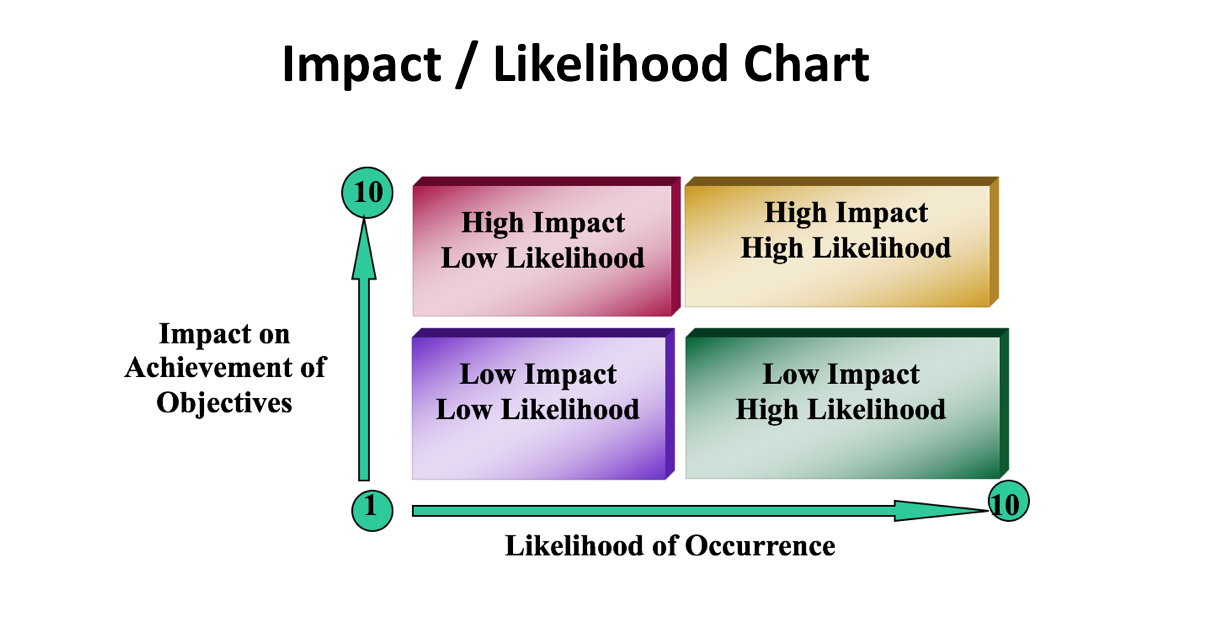
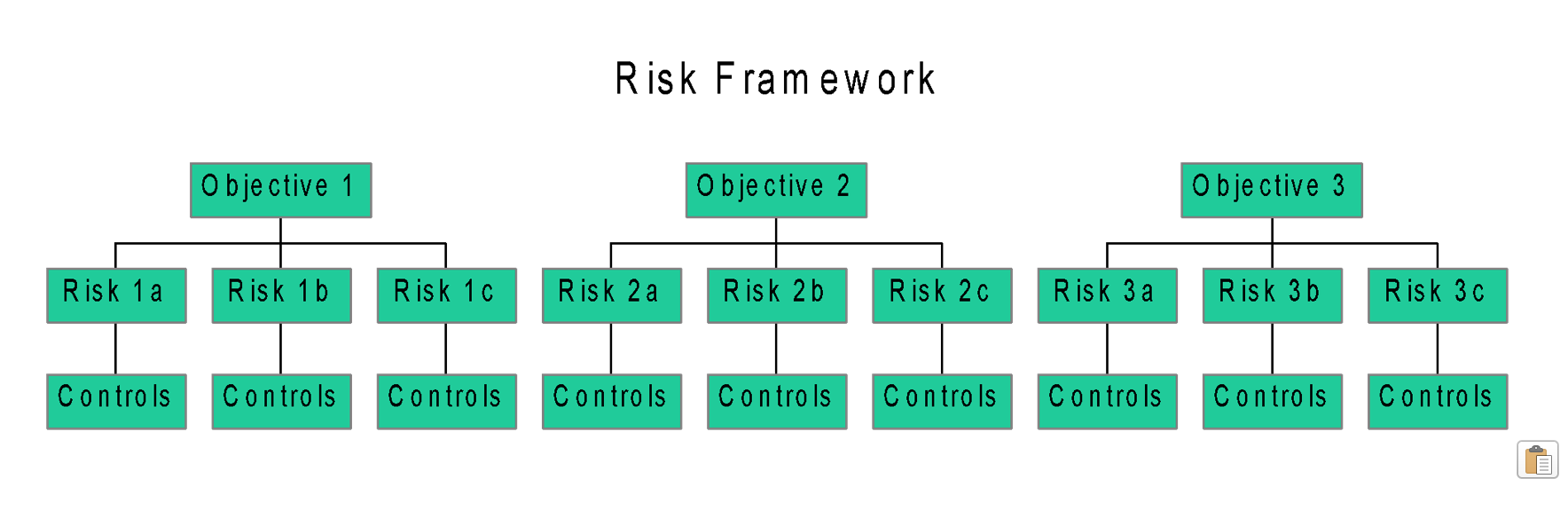
You should then be able to document your risks and related controls like shown in the diagram below: 4. Determine impact and likelihood: In order to identify which risks are most in need of being managed, you need a way to quantify (or at least prioritize) those risks. A common method is to ask employee experts (after they have fully understood the risk history, consequences, and controls) to rank on a scale of 1 – 10 the likelihood of each risk occurring and then to rank on a scale of 1 – 10 the impact that risk would have if it occurred. The resulting rankings can be graphed on a chart like this: 5. Determine whether the exposure is acceptable: For each risk, consider whether internal controls in place reduce the risk to an acceptable level of exposure. This is done by thinking/discussing/understanding the risk’s likelihood of occurring, impact, and internal controls. This step is frequently conducted in a facilitated meeting with employee experts to assure all knowledge and points of view are considered.
6. Develop a risk mitigation plan: For any risks that management considers the exposure to be unacceptable, an action plan should be developed to reduce the exposure to an acceptable level. Below is a list of actions that can be taken to reduce exposure to a risk:
Once you go through the six steps above, you will have a good understanding of your primary risks, controls, and exposures. You will know which risks are being effectively managed and, for the risks not being effectively managed, you will have a high-level action plan to improve the management of those risks. For an in-depth explanation on how to conduct proper risk assessment for implementation projects, please see this blog post. If you have more questions about risk assessment, feel free to reach out to Kevin directly:
kharper@kevinharpercpa.com (510) 593-5037
Comments
|
The Government Finance and Accounting BlogYour source for government finance insights, resources, and tools.
SEARCH BLOG:
Meet the AuthorKevin W. Harper is a certified public accountant in California. He has decades of audit and consulting experience, entirely in service to local governments. He is committed to helping government entities improve their internal operations and controls. List of free Tools & Resources
Click here to see our full list of resources (templates, checklists, Excel tools & more) – free for your agency to use. Blog Categories
All
Need a Consultation?Stay in Touch! |
Search Across Entire Site:
HELPFUL LINKS:
|
461 2nd Street, #302
San Francisco, CA 94107 (510) 593-5037 KHarper@kevinharpercpa.com |


 RSS Feed
RSS Feed